source: AZ500-AzureSecurityTechnologies
- Exercise 1: Deploy an Azure virtual machine
- Exercise 2: Create a Log Analytics workspace
- Exercise 3: Create an Azure storage account
- Exercise 4: Create a data collection rule.
Exercise 1: Deploy an Azure virtual machine
In Azure open cloudshell and select PowerShell
Run the following to create a resource group that will be used in this lab:
New-AzResourceGroup -Name AZ500LAB131415 -Location 'EastUS'Run the following to enable encryption at host (EAH)
Register-AzProviderFeature -FeatureName "EncryptionAtHost" -ProviderNamespace Microsoft.Compute Run the following to create a new Azure virtual machine.
New-AzVm -ResourceGroupName "AZ500LAB131415" -Name "myVM" -Location 'EastUS' -VirtualNetworkName "myVnet" -SubnetName "mySubnet" -SecurityGroupName "myNetworkSecurityGroup" -PublicIpAddressName "myPublicIpAddress" -PublicIpSku Standard -OpenPorts 80,3389 -Size Standard_DS1_v2 When prompted for credentials:
| User | localadmin |
| Password | Please use your personal password |
Wait for deployement to complete, run the following to confirm that the virtual machine named myVM was created and its ProvisioningState is Succeeded.
Get-AzVM -Name 'myVM' -ResourceGroupName 'AZ500LAB131415' | Format-TableExercise 2: Create an Log Analytics workspace
On the azure top search bar type log analytics and select log analytics > + Create
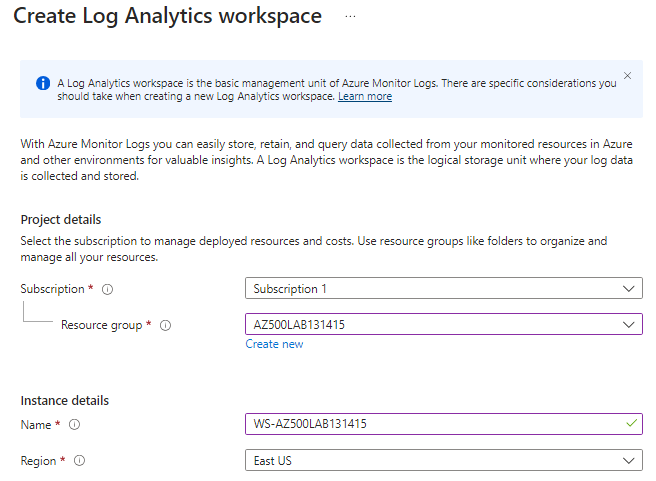
We will use the following values
| Subscription | the name of the Azure subscription you are using in this lab |
| Resource group | AZ500LAB131415 |
| Name | any valid, globally unique name |
| Region | East US |
Exercise 3: Create a Data Collection Rule
On the azure top search bar type montior and select monitor
Go to settings section of the side bar > select data collection rules > create
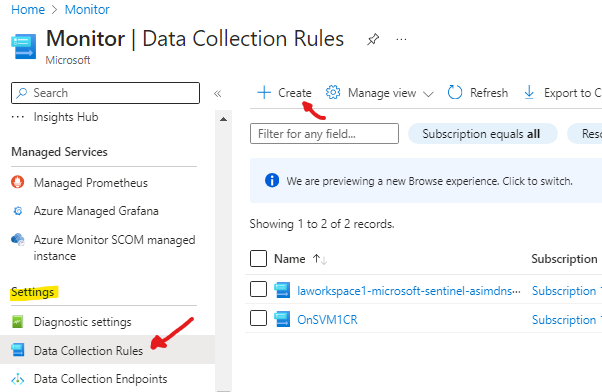
use the following settings
| Rule Name | DCR1 |
| Subscription | the name of the Azure subscription you are using in this lab |
| Resource Group | AZ500LAB131415 |
| Region | East US |
| Platform Type | Windows |
| Data Collection Endpoint | Leave Blank |
click next to go to the resources tab > click add resources > select AZ500LAB131415
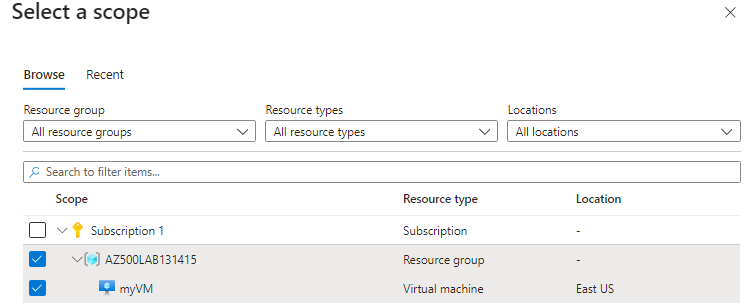
click the Enable Data Collection Endpoints
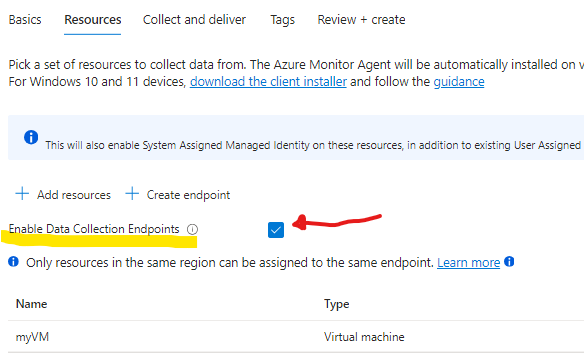
click next to go to Collect and Deliver tab > click add data source > select Performance Counters > select Basic and click on Destination >
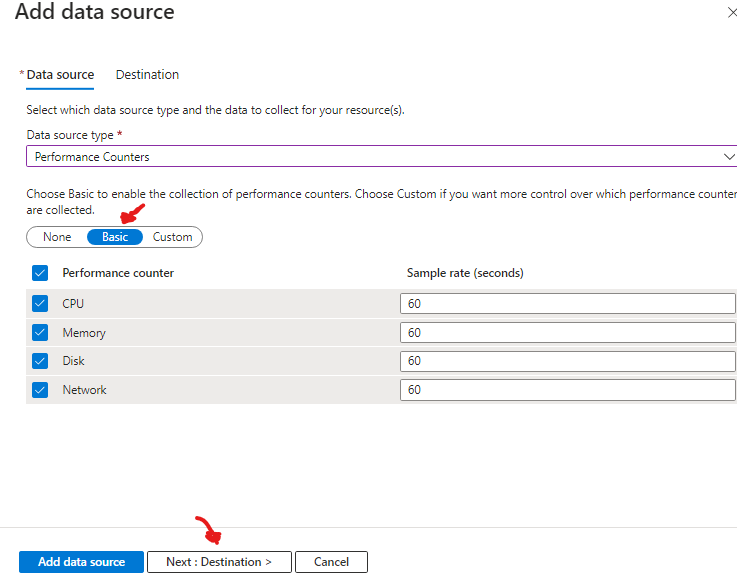
Click + Add destination > select Destination type: Azure Monitor Logs > Subscription: use your subscription > Destination details: use the workspace you previously created
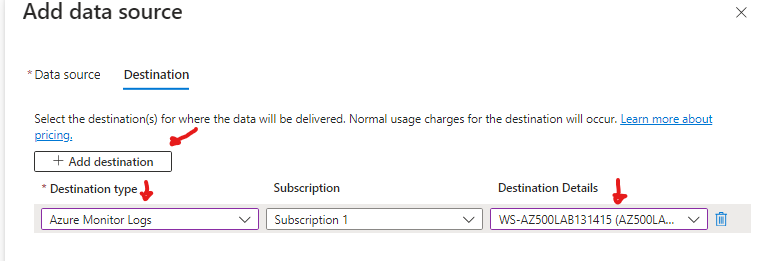
Click add data source, click review and create, and go ahead and create.
Results: You deployed an Azure virtual machine, Log Analytics workspace, Azure storage account, and a data collection rule to collect events and performance counters from virtual machines with Azure Monitor Agent.
Note: Do not remove the resources from this lab as they are needed for the Microsoft Defender for Cloud lab and the Microsoft Sentinel lab.
