source: https://learn.microsoft.com/en-us/azure/sentinel/tutorial-enrich-ip-information
- Create Playbook
- Authorize connections on Logic Apps
- Authorize Log Analytics connections
- Create Automation rule
Prerequisites
An Azure user with the following roles:
Microsoft Sentinel Contributor on the Log Analytics workspace where Microsoft Sentinel is deployed.
Logic App Contributor, and Owner or equivalent, on whichever resource group will contain the playbook created in this tutorial.
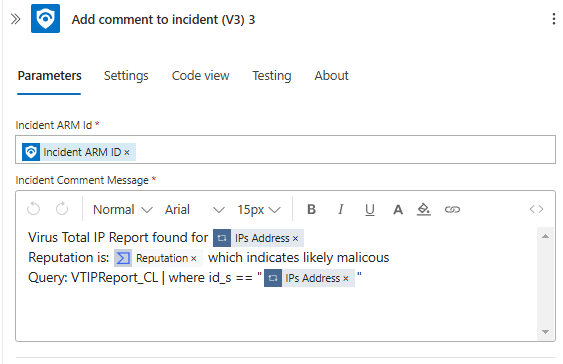
Installed VirusTotal Solution from the Content Hub
A (free) VirusTotal account will suffice for this tutorial. A production implementation requires a VirusTotal Premium account.
An Azure Monitor Agent installed on at least one machine in your environment, so that incidents are generated and sent to Microsoft Sentinel.
Create Playbook
First we need to install the VirusTotal Solution from the Content Hub on Sentinel, go to Content Hub and install it.
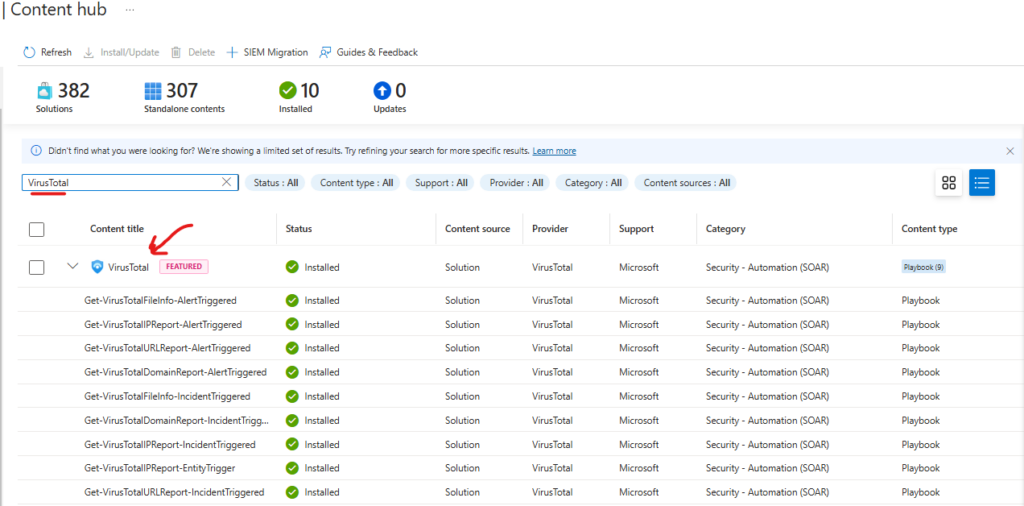
Now click on Automation on the Sentinel left side menu, select Playbook Templates
this will display a list of templates available, select: IP Enrichment – Virus Total report – Incident Triggered
and click create playbook
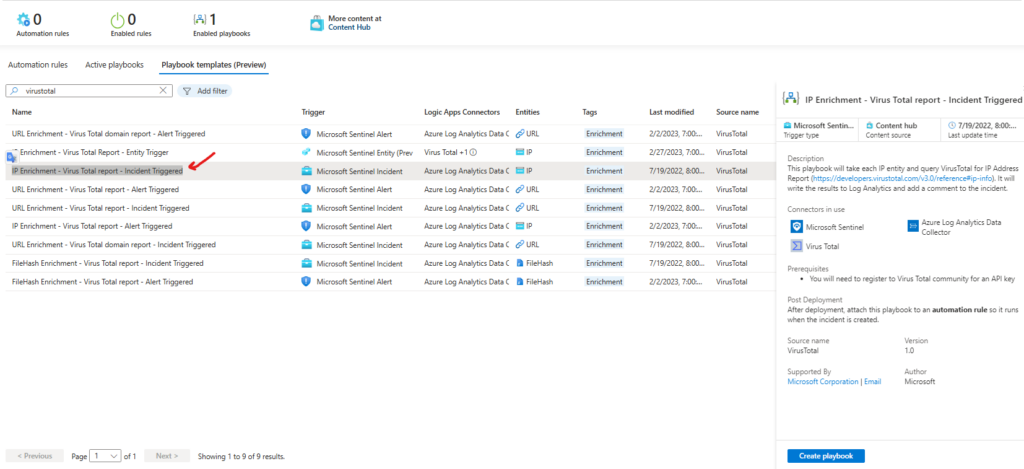
select your subscription, resource group and playbook name for your playbook
leave the Enable diagnostics for log analytics unchecked and click Next
on connections click next, and click create playbook.
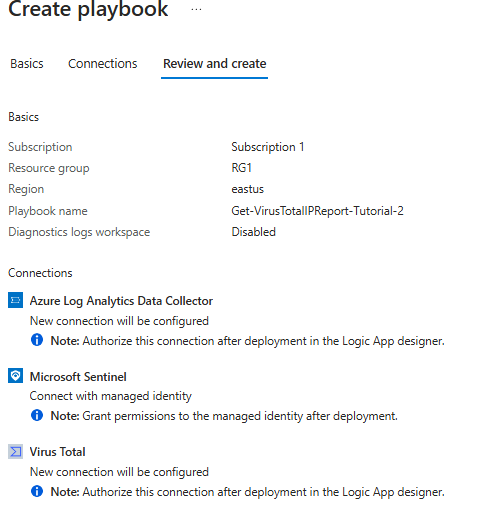
Authorize connections on Logic Apps
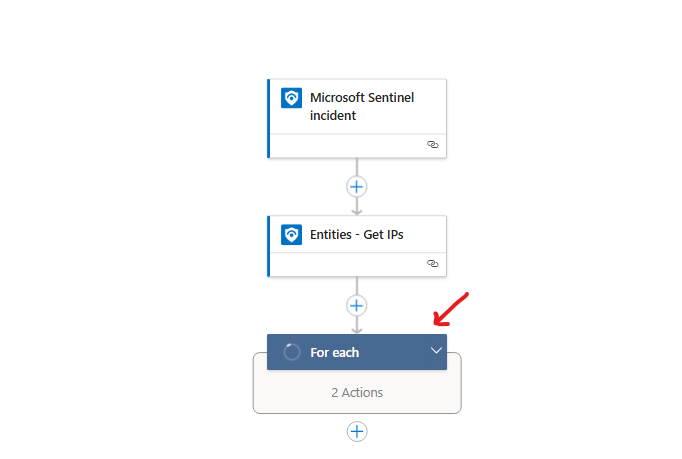
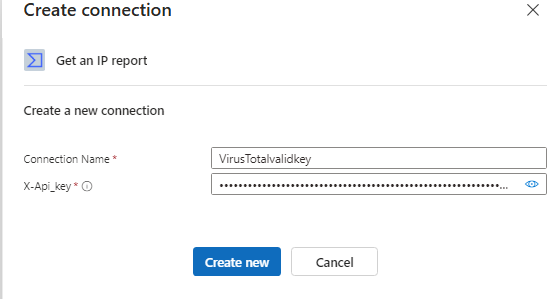
we will start by clicking on the for each condition, select the Get an IP report, then click on Change connection > then click on add new > then add a name and enter your VirusTotal API Key
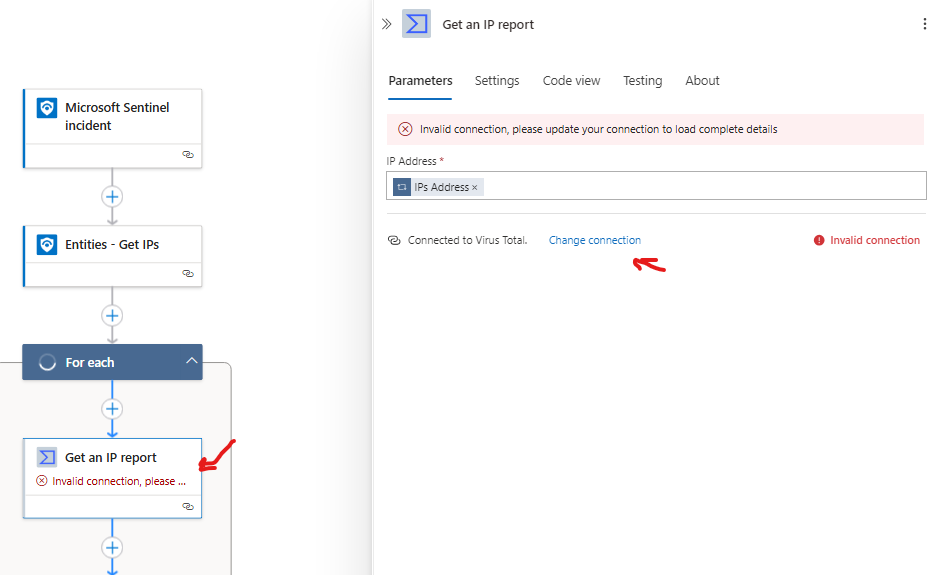
Authorize Log Analytics connections
Now we will click on the condition step.
This condition checks if reputation of IP is greater or equal than 0. If this is True then it will proceed on the True path of the automation, if False it will proceed on the False path of the automation.
As we can see we need to fix the Invalid connection on both Send Data and Send Data 2
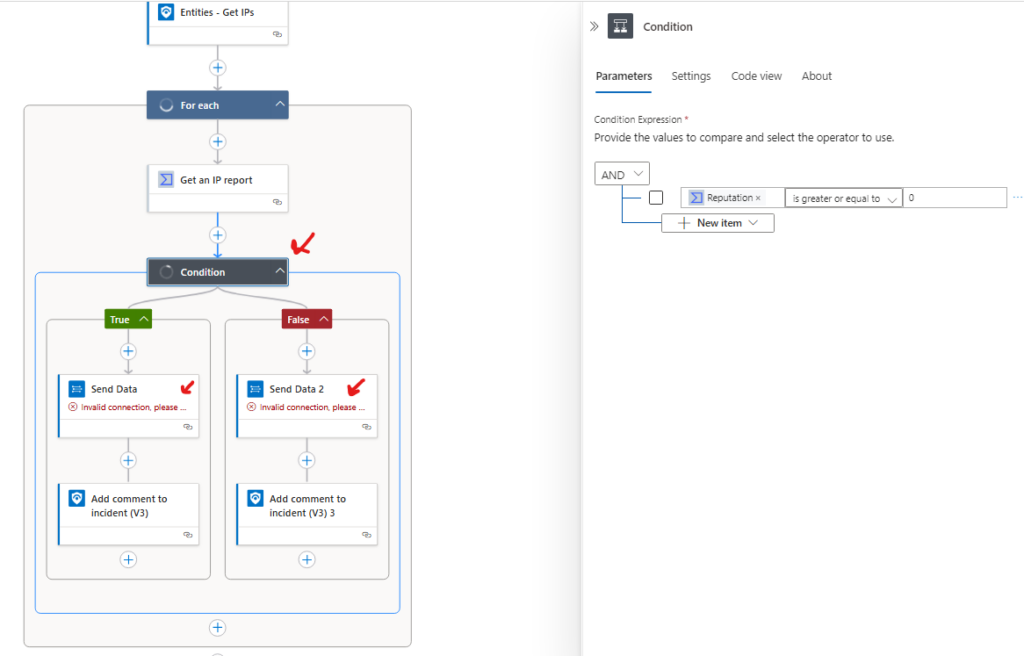
Click on Send Data and click change connection, this will
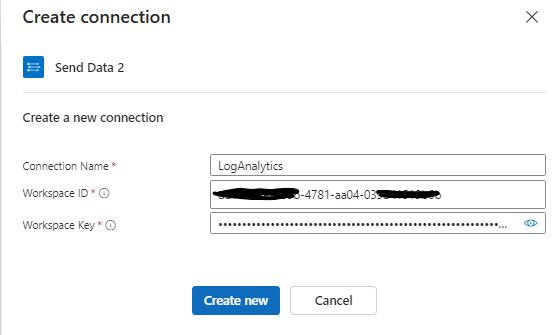
You will need your LogAnalytics Worspace ID and Key which you can find on Log Analytics>(your workspace name)> under the Settings tab select Agents.
Once entered go ahead and click Create new
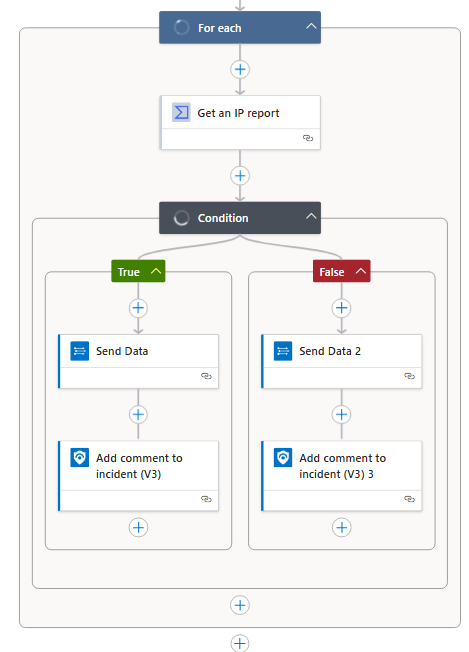
now click save to save the Workflow, the playbook should be now configured properly and should look like this
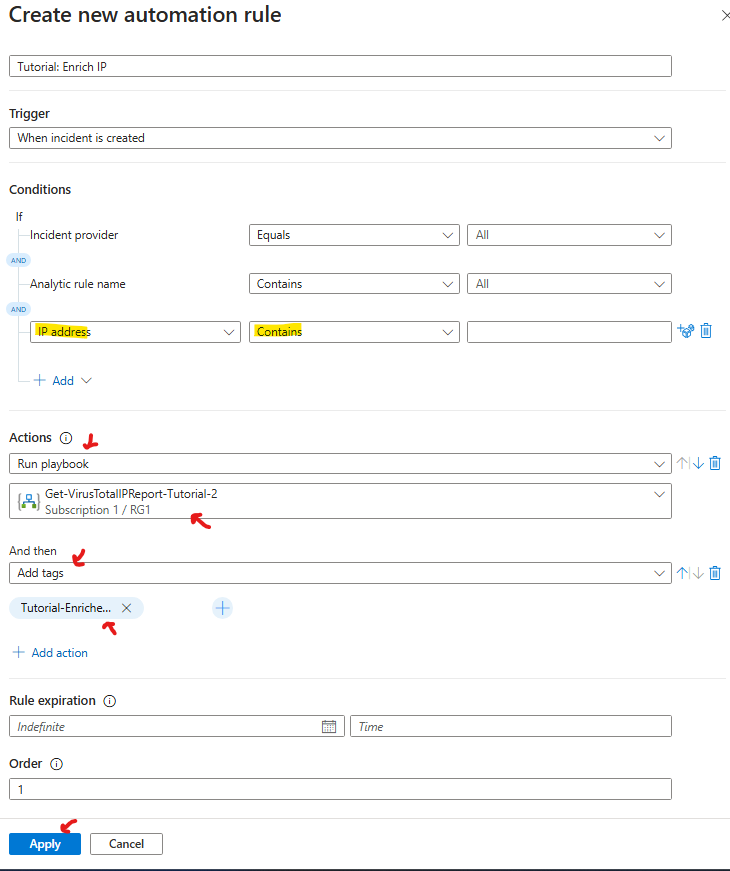
Create Automation Rule
In order to run the created playbook we will need to create an automation rule to run it.
We will now go to Sentinel > Automation > select create Automation rule
Under Conditions
add IP address select Contains and leave black (meaning will apply to all ip addresses)
Under Actions
we will select Run Playbook
select the playbook we created previously
we will also add an And then conditon, select add tags, underneath click on the + button and enter the name of the playbook
Now we can click on apply
Now any incident containing the attacker IP address will be enriched with data from VirusTotal and a message will be added to the incident indicating whether it’s a possible threat or not based on the IP reputation score.