Header Analysis
In this example we have a phishing email impersonating CIBC, we will conduct a header investigation.
Right away we can see that email sender (CIBC-Banking.Service.Email.8@caib.com) does not match with cibc.com, and is already looking suspicious.
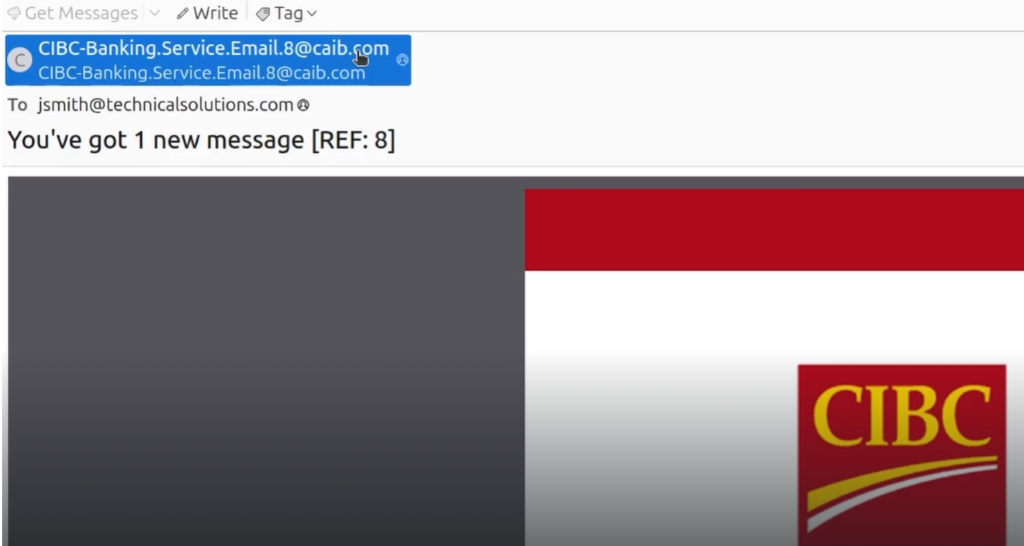
We now will open the .eml file of the email using a text editor, in this case I am using sublime text to inspect the email header.
We can see Return-Path is set to a different email in this case meztaz.logocec8@caib.com instead of CIBC-Banking.Service.Email.8@caib.com
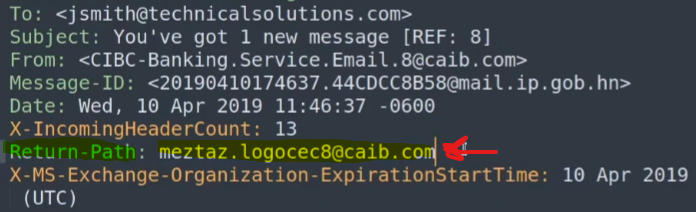
If we look at the X-Sender IP or continue looking through the email headers
We’ll notice the IP address of 190.6.201.67 which we can further investigate
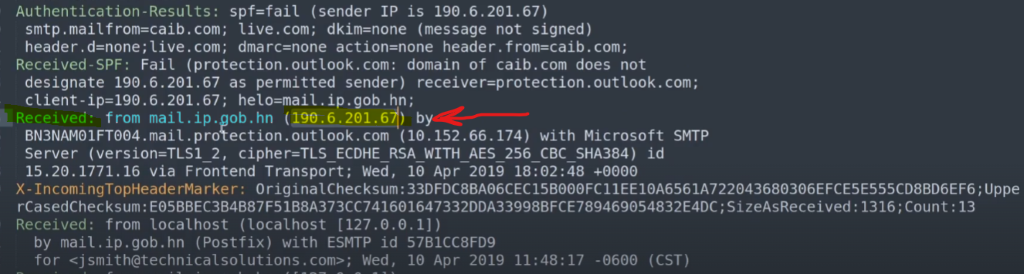
We can do a WHOIS lookup and we can see this IP address is location is in Honduras and is affiliated with CABLECOLOR which is not related to CIBC bank.
Attachment Analysis
In this example we are assuming we have already extracted the suspicious attachment, in this case it’s a file named quotation.iso.
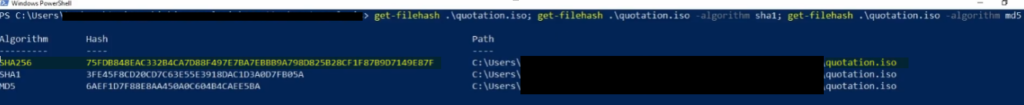
Now we will get the hash of the file for further investigation.
On Windows PowerShell we can go to the file directory and run get-filehash cmdlet as in the following example:
get.filehash .\quotation.iso -algorithm sha256
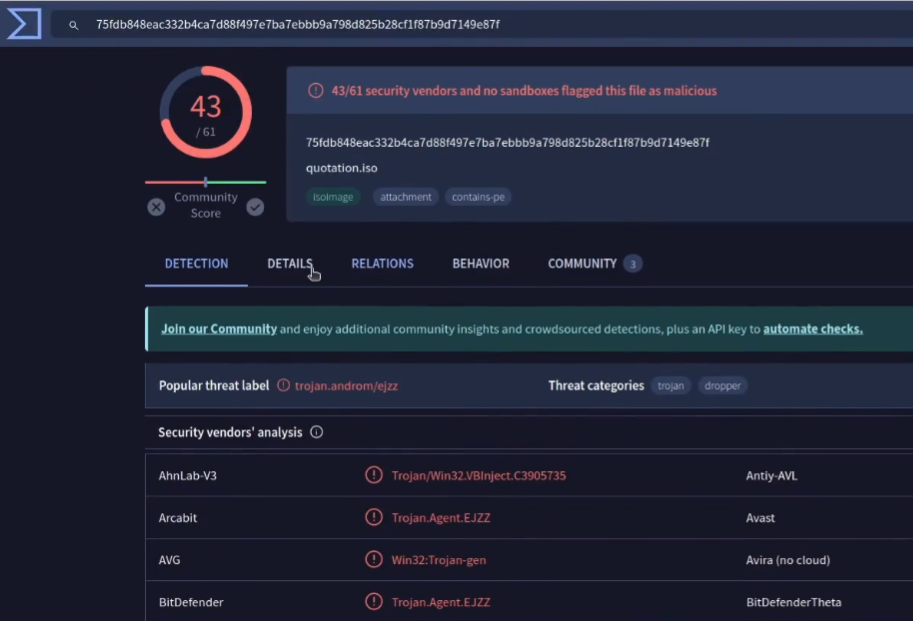
Now that we have extracted the hash we can run it on reputation and malware analysis services.
We can see on VirusTotal 43/61 Security vendors have flagged this hash as malicious and the popular threat label for this hash is trojan.androm/ejzz
In the Details tab
We can look when it was first submitted and other names of this file
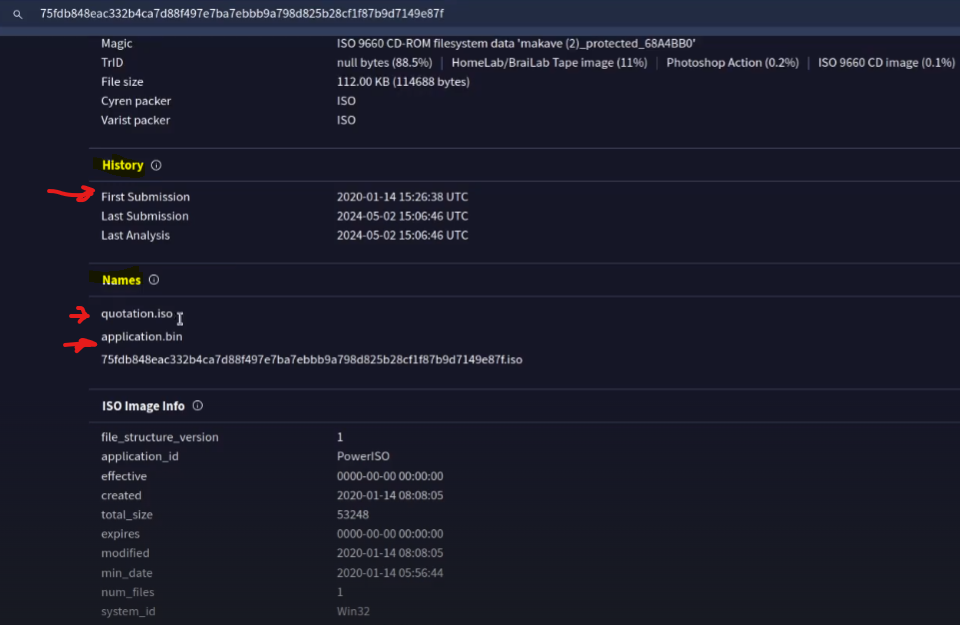
We can safely conclude attachment is deemed a known malicious trojan.
