source: SC-200T00A-Microsoft-Security-Operations-Analyst
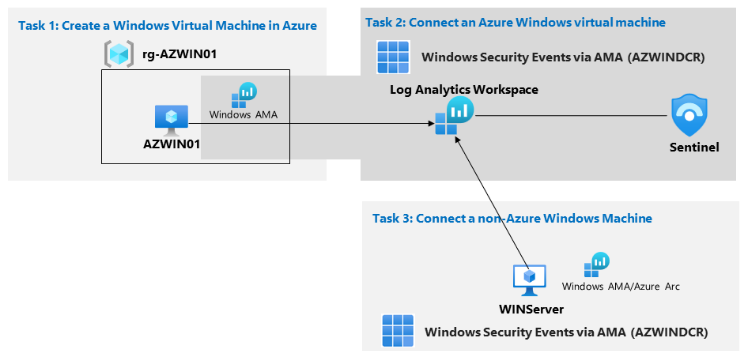
Task 1: Create a Windows VM in Azure
Go to Marketplace, search for Windows 10 machines, select the Windows 10 Enterprise, version 22H2 option.
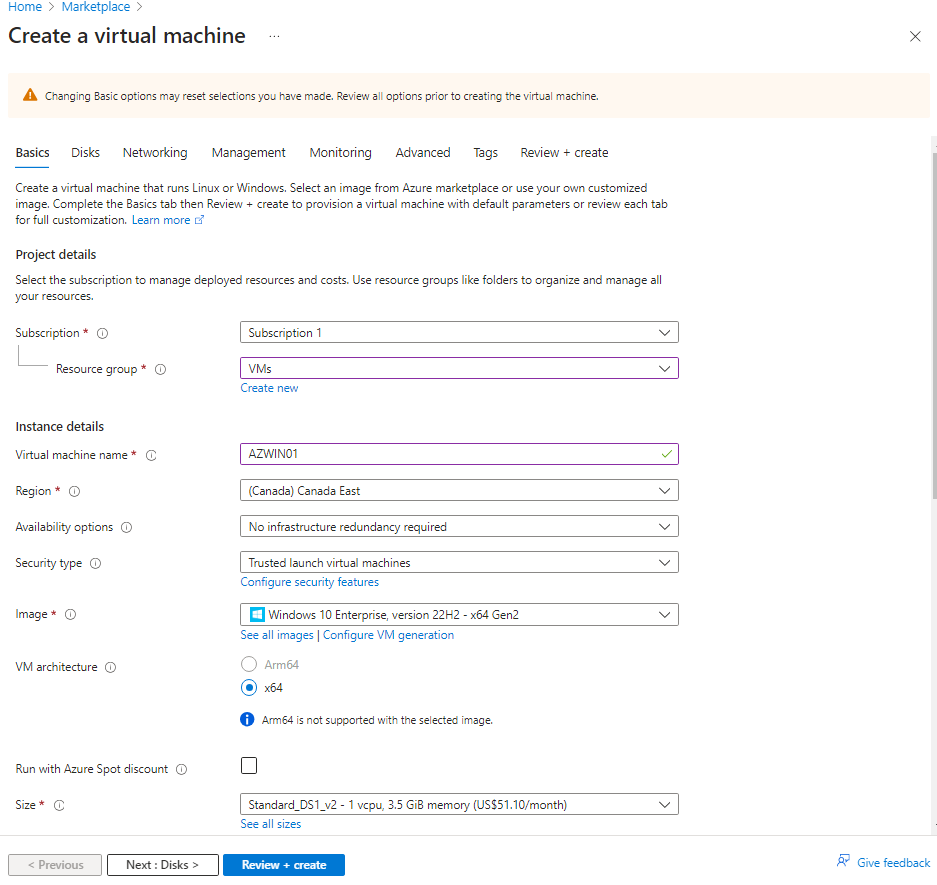
Use pre configured settings as seen below, add user name and password for the administrator account of the vm and proceed to create.
Task 2: Connect Azure Windows VM via AMA
Go to Microsoft Sentinel > Data Connectors > Content Hub and search for the Windows Security Events solution and select it from the list and select install.
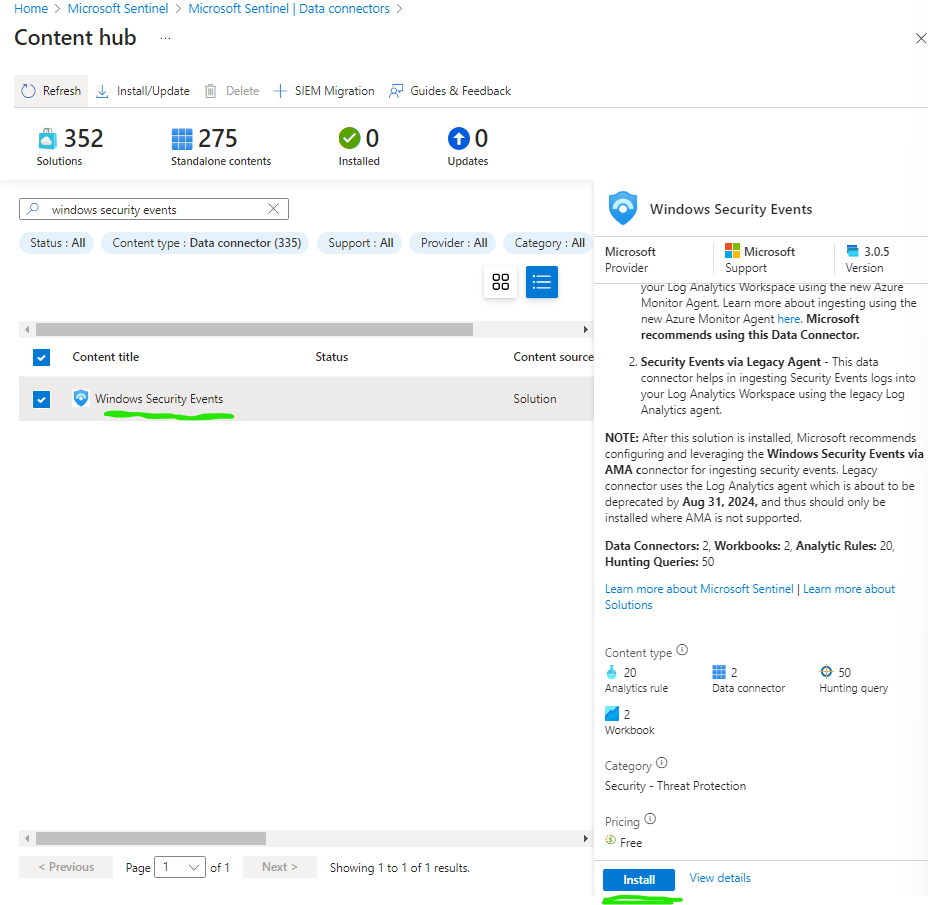
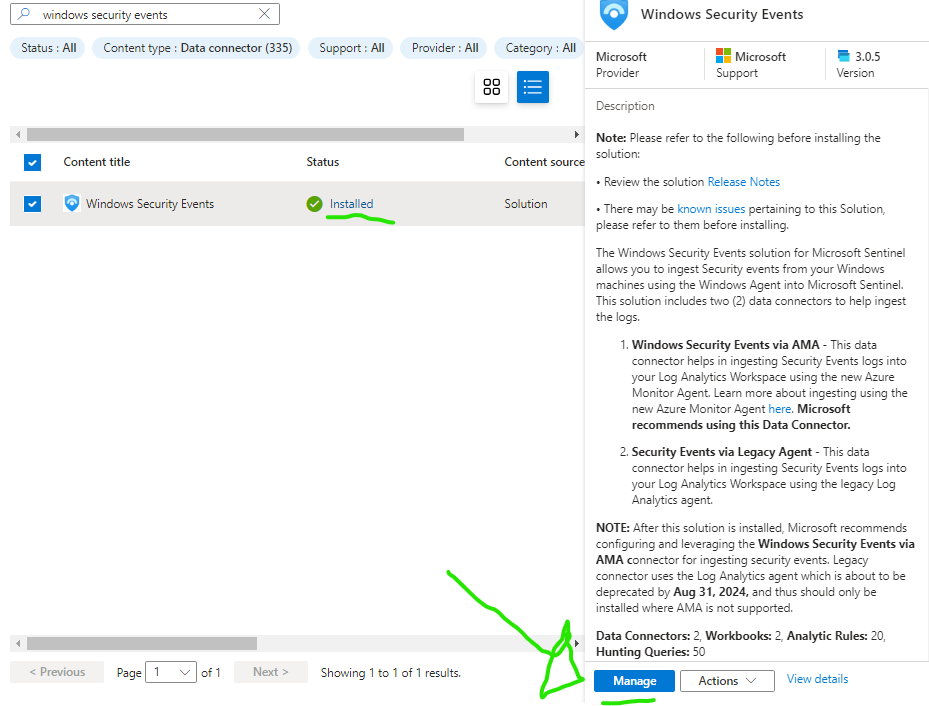
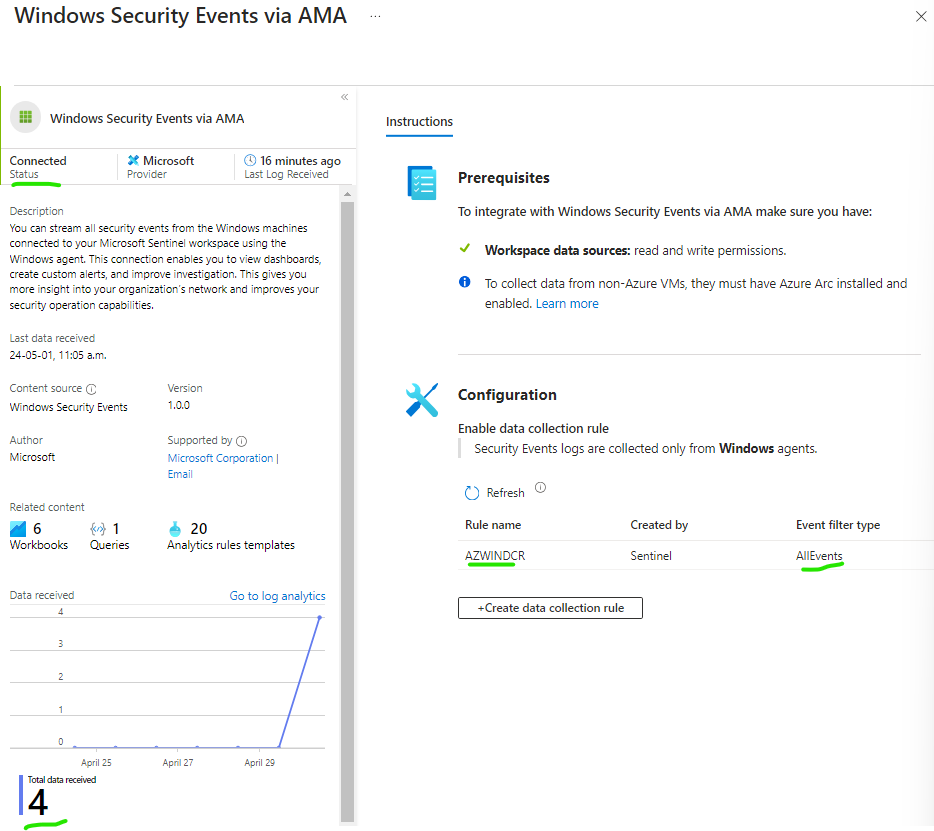
Once installed select Manage, select Windows Security Events via AMA and click Open connector page, then select +Create data collection rule.
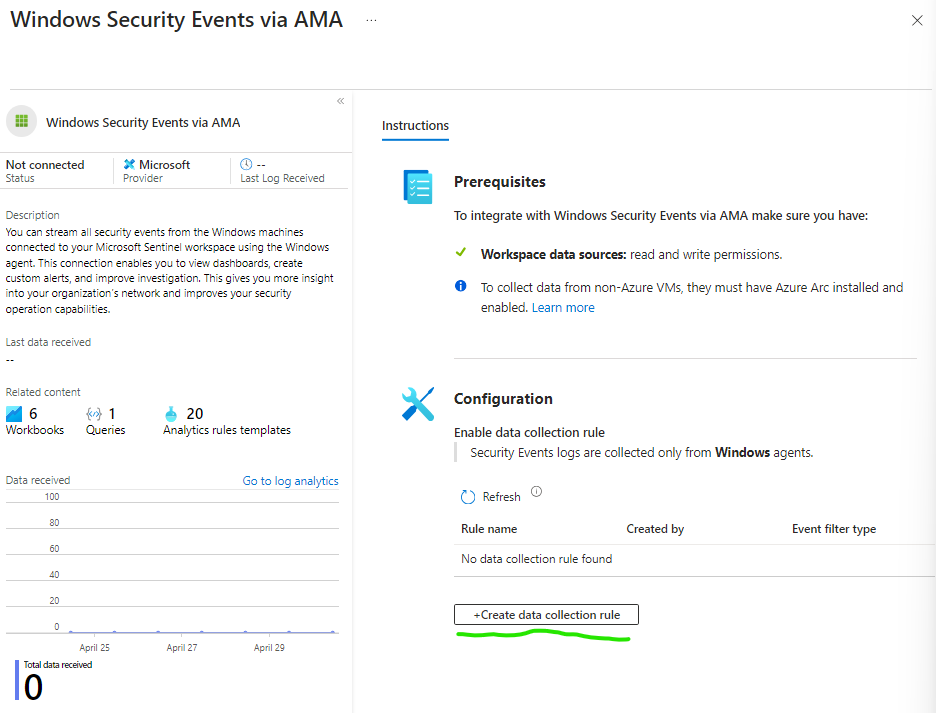
Give the Collection Rule a name in this case it will be named AZWINDCR, select the resource group where your previously created VM is located.
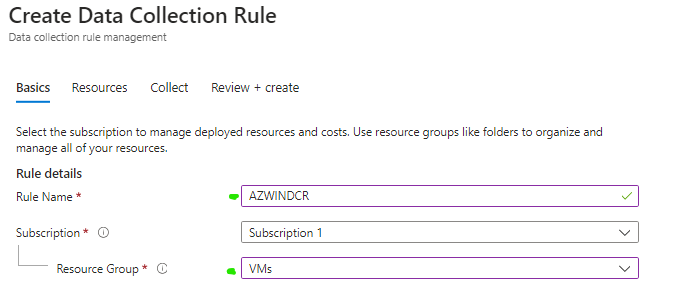
On the Resources tab, select add resources and select the VM we created previously, click apply once selected.
On Collect tab we will select All Security Events, then proceed to create the Collection Rule, wait a couple of minutes and refresh the page until you see the status change to Connected.
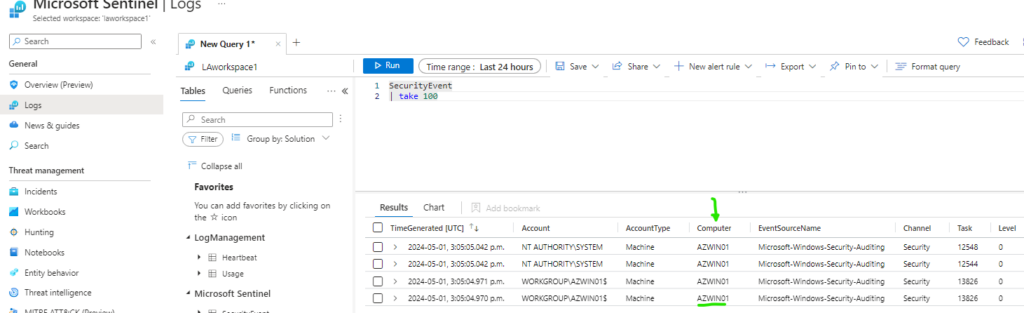
If we go to Sentinel > Logs and run a query on the SecurityEvents table we can see we are receiving security data from our Azure Windows VM AZWIN01
Task 3: Connect a non Azure VM
In this case I am onboarding a Windows VM deployed on VMware on my onsite pc.
Go to Azure Arc, select Add resources > under Machines select Add/Create > Add a machine, select Add a single server and click Generate script.
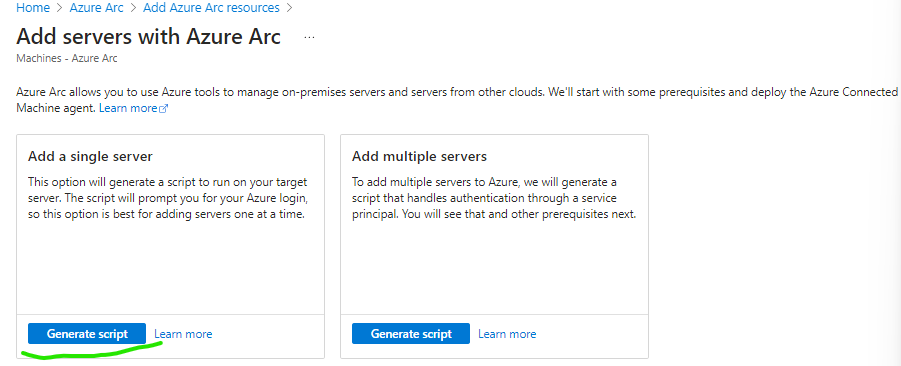
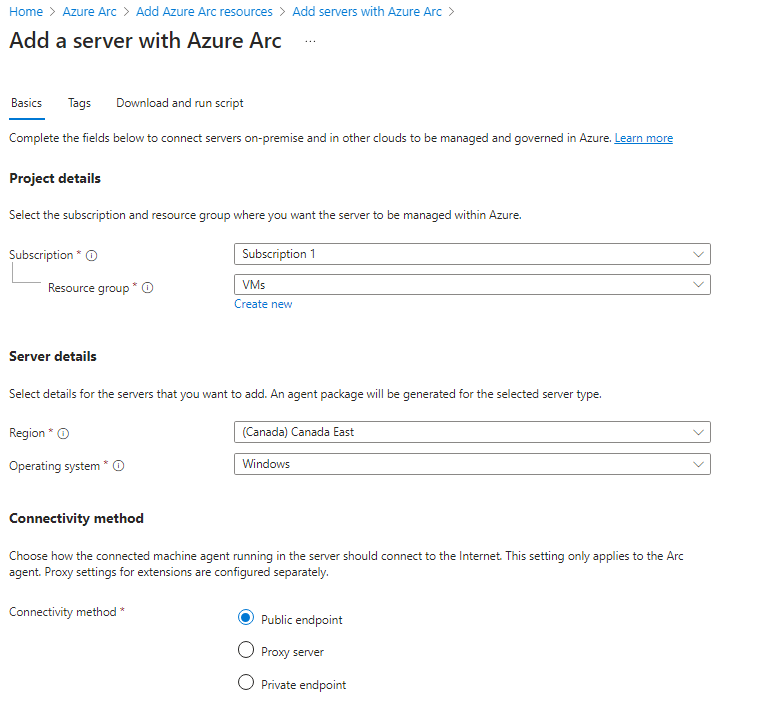
Fill out the Resource group and Region the VM will be onboarded to. Click Download and run script.
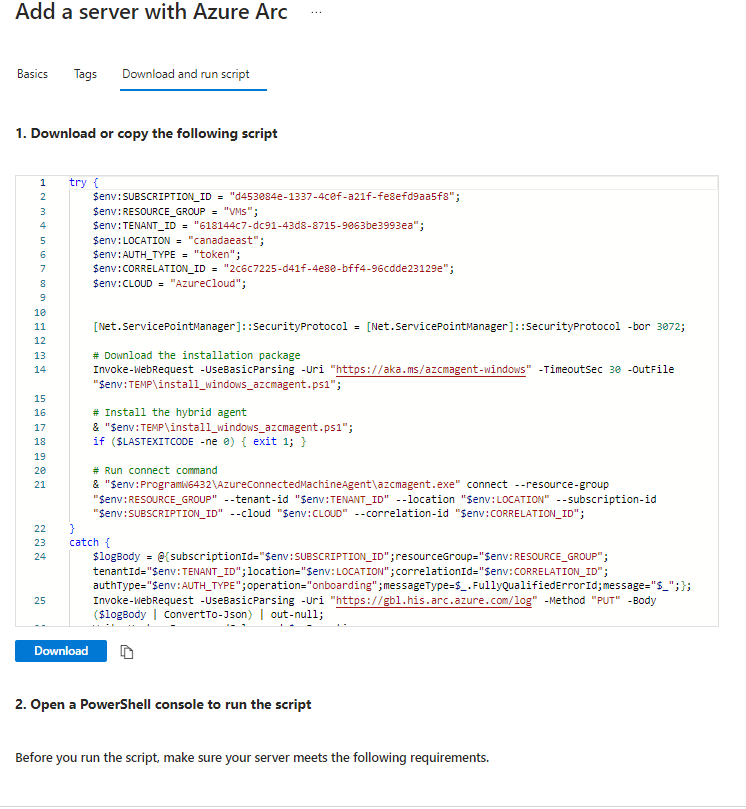
In my case I will copy the script and run it on PowerShell in my VM.
you will need to change PowerShell execution policy to disabled in order to run the Arc script. To do so do the following:
– Open PowerShell as Administrator
– Run the following command
Set-ExecutionPolicy Unrestricted
Now we can run our PowerShell script to install Azure Arc
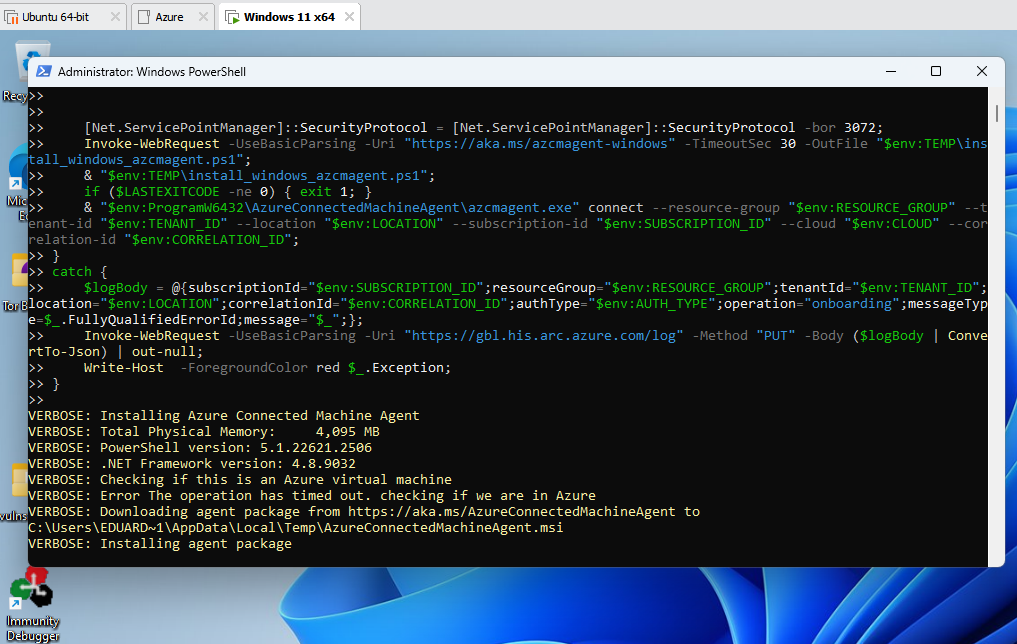
You will get prompted to authenticate with Azure, enter credentials of the user you would like to use.
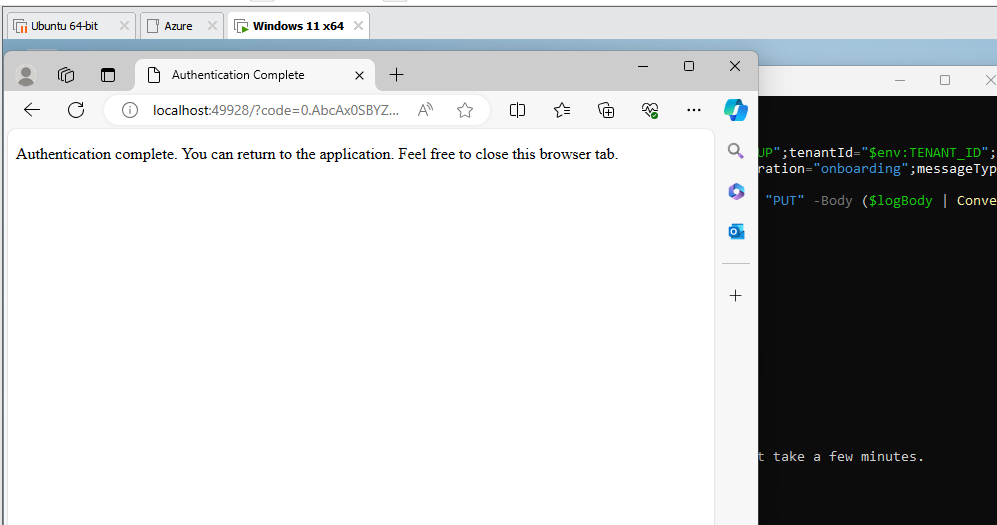
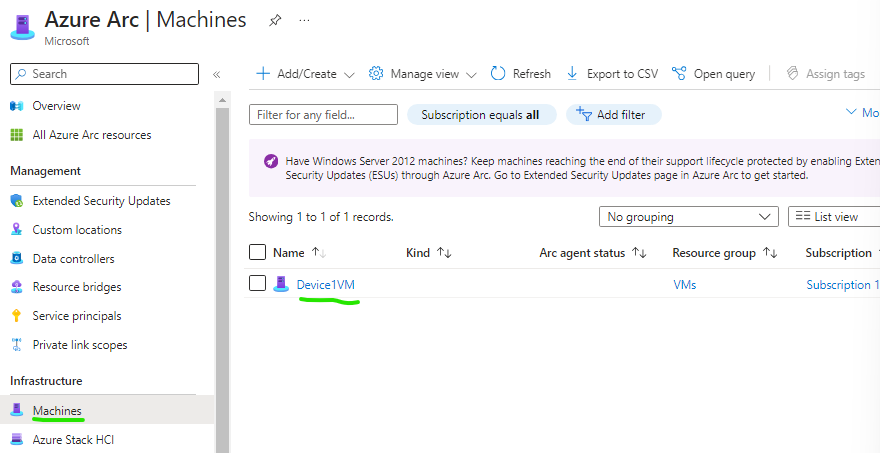
We can see that the onsite VM now has been onboarded with Azure Arc and shows on under Machines
We can change the execution policy back to restricted using the following command on PowerShell on Administrator mode on the VM:
Set-ExecutionPolicy Restricted
We can now go to Sentinel > Data connectors > Windows Security Events via AMA > click Open Connector page and then click > Create data collection rule
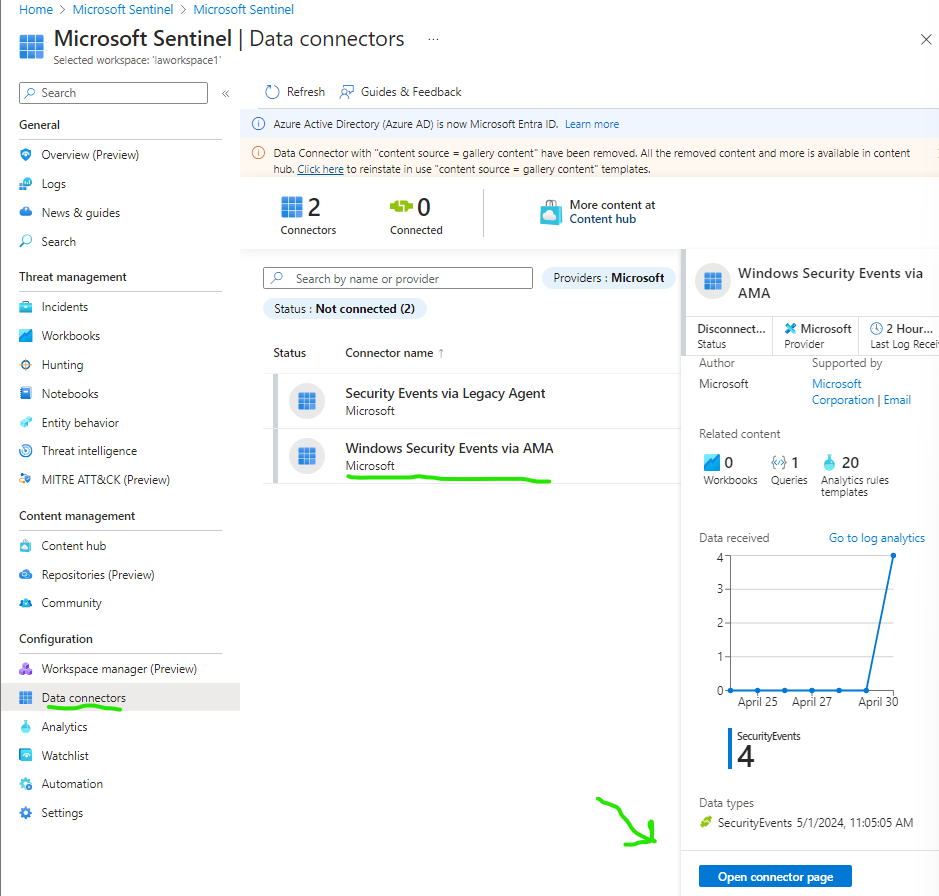
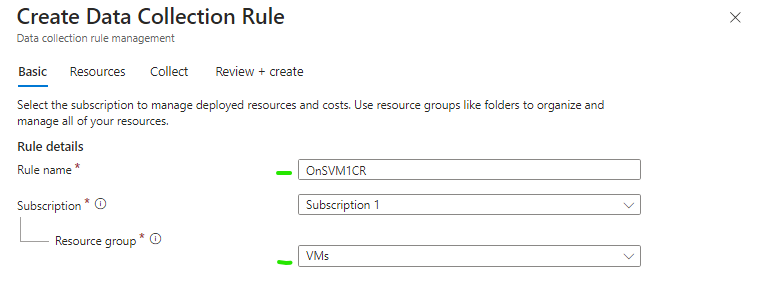
We will create a Data collection rule for the on-site VM.
Give the Rule a name and select the Resource group your VM is located at.
Select your Azure Arc onboarded VM
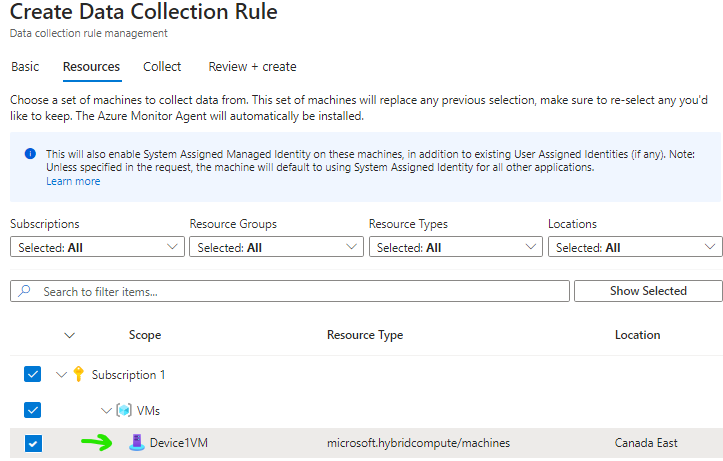
On the Collect tab we will select All Security Events, and we can proceed to create.
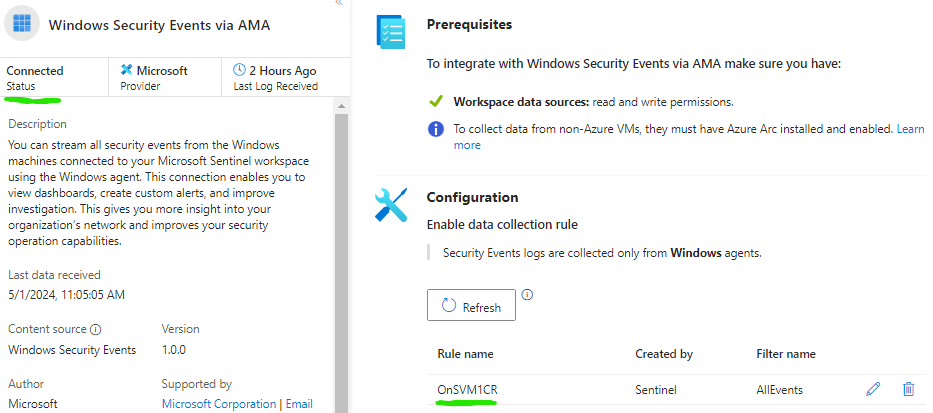
We can see that Windows Security Events via AMA is now connected.
