source: SC-200T00A-Microsoft-Security-Operations-Analyst
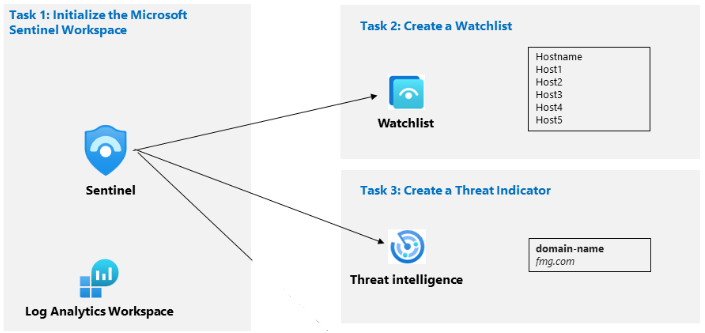
Task 1: Initialize the Microsoft Sentinel Workspace
go to Log Analytics Workspace and create a new analytics workspace for your Sentinel deployment
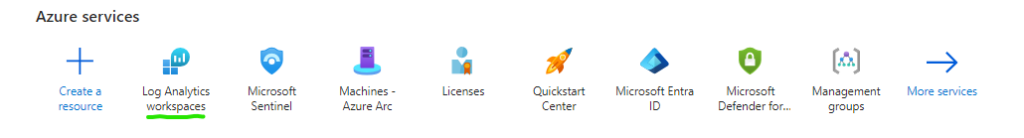
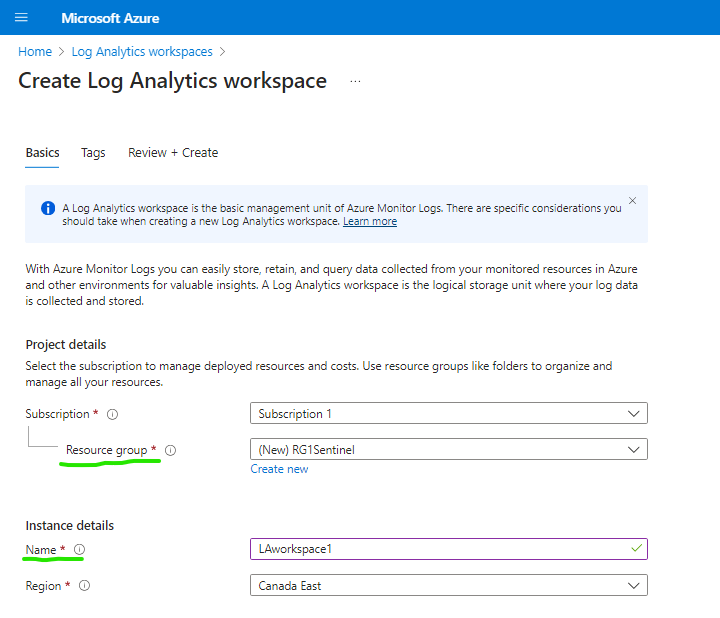
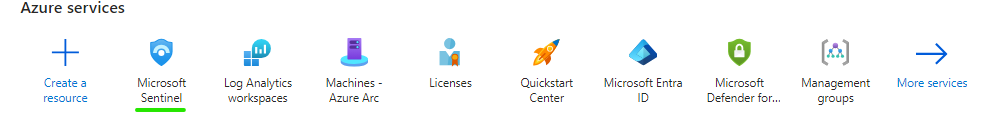
Once the log analytics workspace is created we can click sentinel from azure services to create a sentinel deployment within the previously created workspace
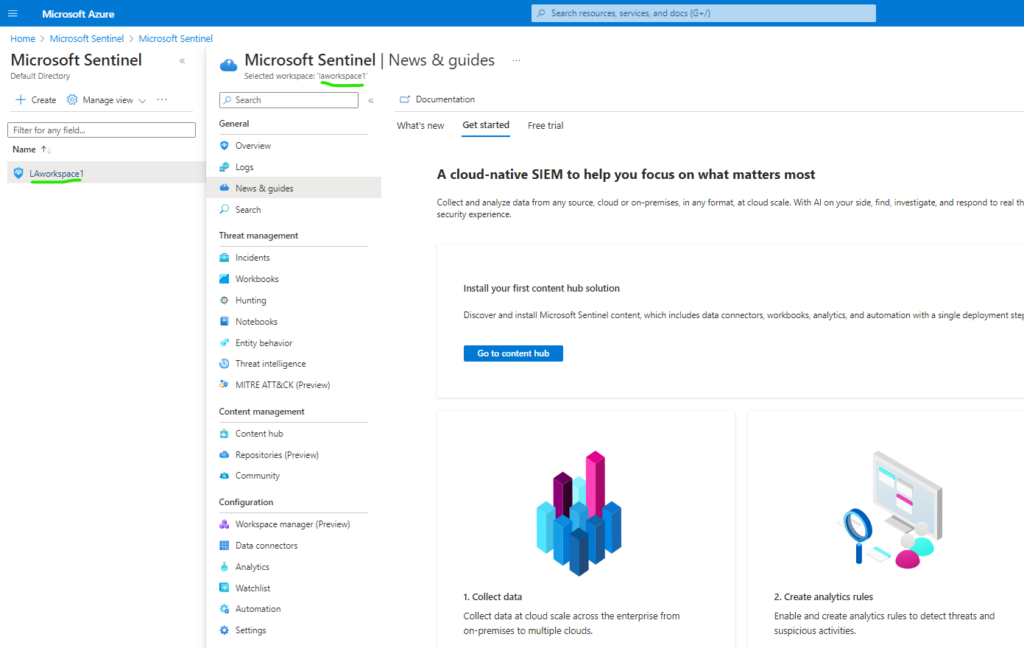
Click add to workspace (select workspace created) and you should have successfully deployed Sentinel in you Azure enviroment.
Task 2: Create a Watchlist
Open notepad and add the following hostnames

go to File > Save as > Highvalue.csv
now we will upload the saved csv file containing the hostnames we want to specially keep an eye on, to our watchlist by selecting watchlist from the sidebar and selecting new
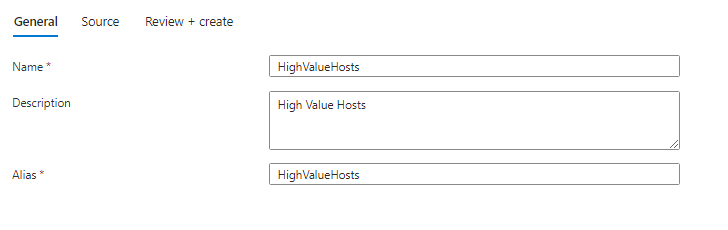
Add name, description and alias for the watchlist
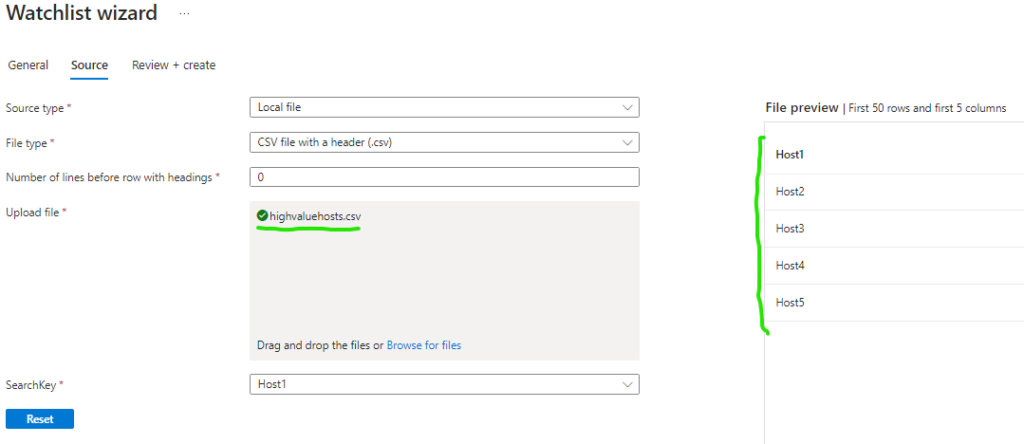
upload csv file and create watch list.
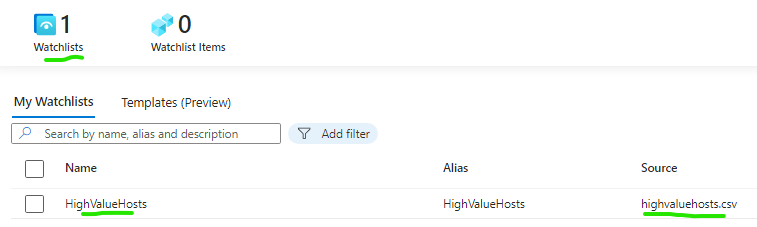
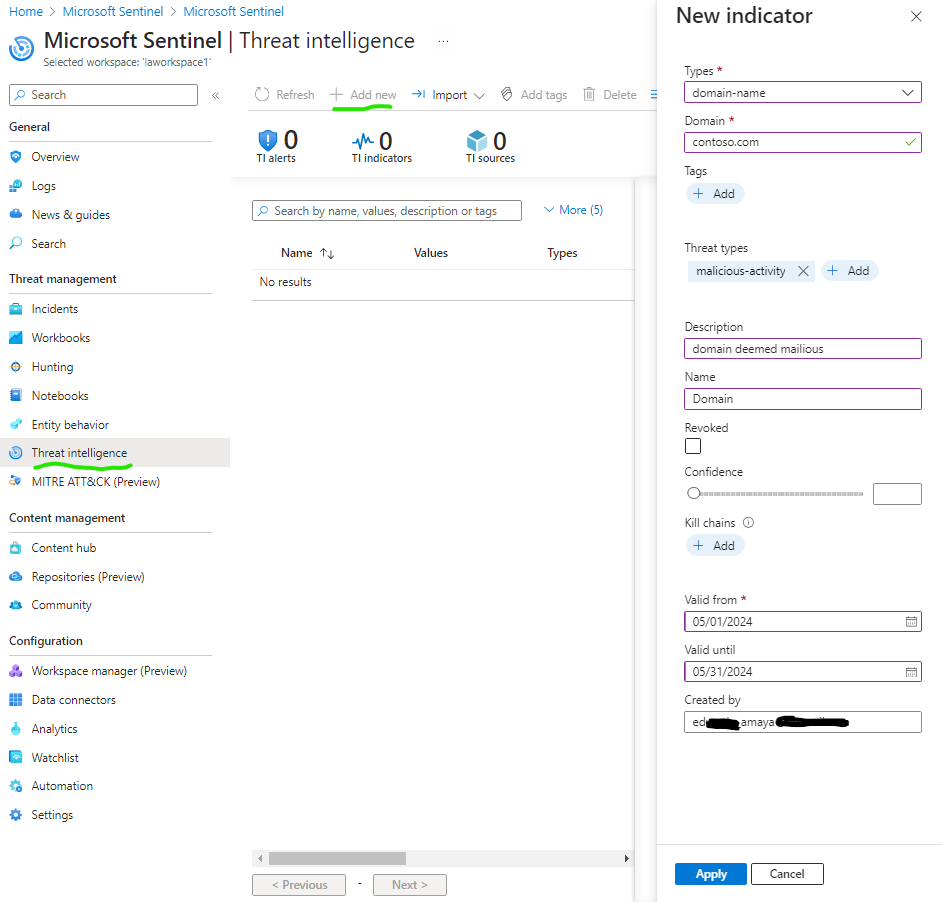
Task 3: Create a threat indicator
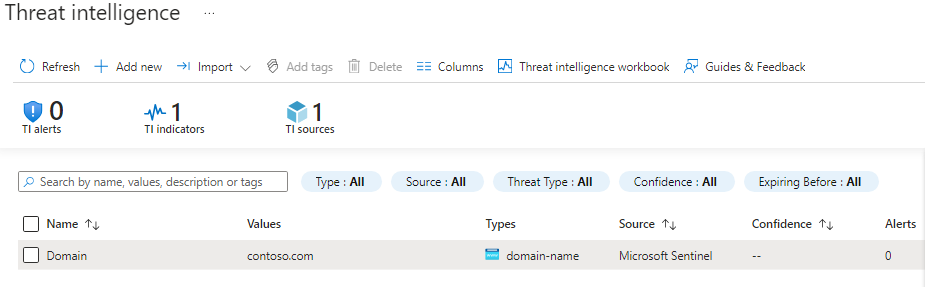
Go to Threat intelligence on the Sentinel sidebar, select Add new, fill out indicator information in this example will be a malicious domain name contoso.com