Step by step example of a basic credentialed scan on a target VM with vulnerable software installed on it in my lab environment.
Scenario:
VM – Target
OS: Windows 10 evaluation
- outdated Firefox
- outdated Chrome
- outdated 7zip
OS: Kali Linux
Nessus – Essentials
Select create a new scan
Click on Basic Network Scan
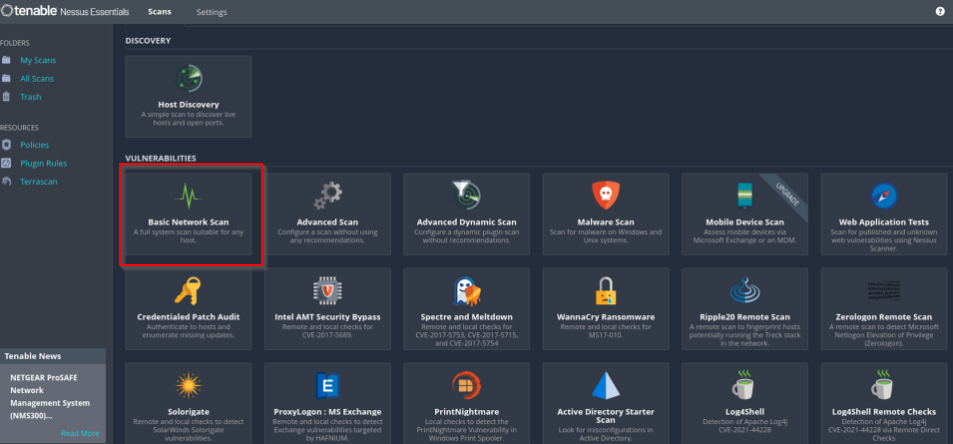
Fill out name, description, targets
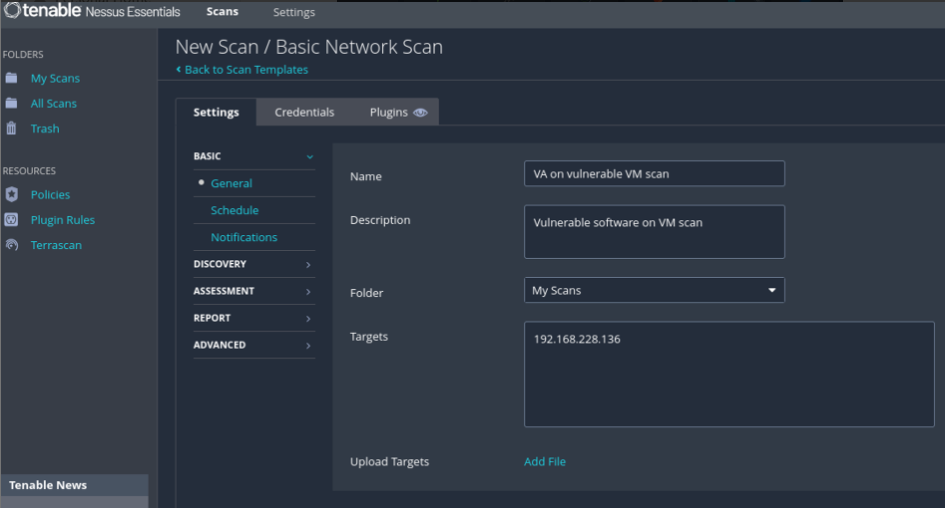
Go to Credentials tab.
Select required authentication method and credential information for target host
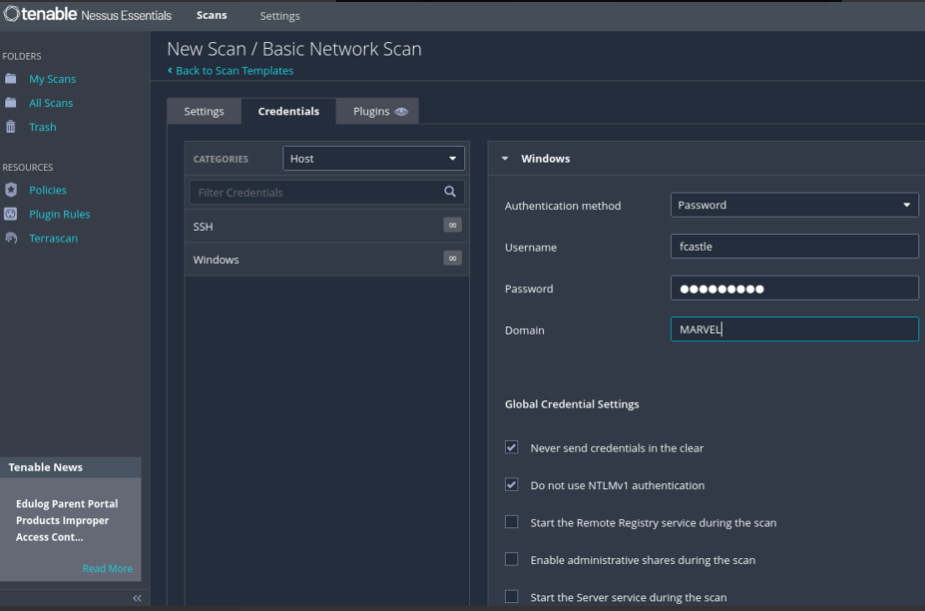
Save configuration and launch scan
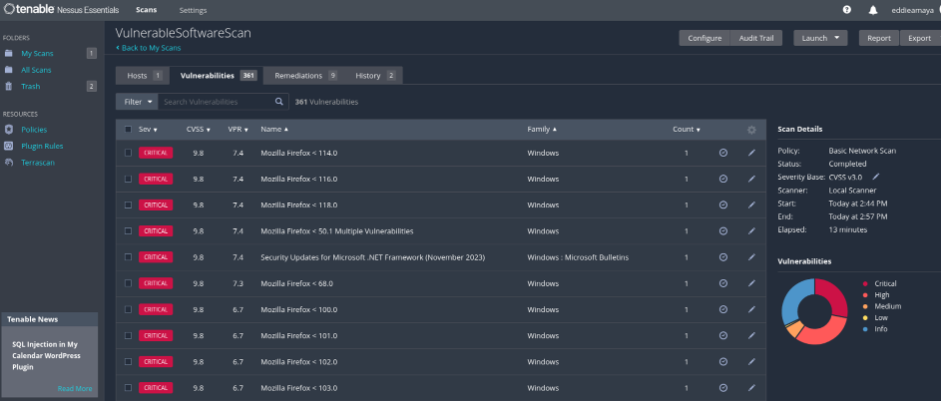
Tenable Nessus Essentials basic credentialed scan results:
28 Critical, 32 High and 7 Medium vulnerabilities detected.
Recommended remediation actions:
Update vulnerable software to latest release (if not vulnerable) or remove vulnerable software from identified assets.
