Here we will conduct an investigation of one of the attacks conducted against our previously deployed Azure VM Honeypot.
Select Kibana from the menu
we will select and open T-pot dashboard
scroll down to the bottom of the dashboard and select a CVE you would like to investigate, hover your mouse on top of the cve until a + symbol appears, click it so we can isolate all the information gathered in relation to this attack
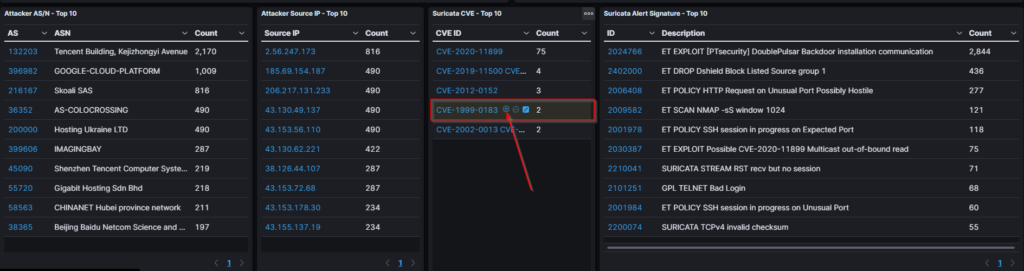
this would allow to gather attacker source IP address, attack description, etc.
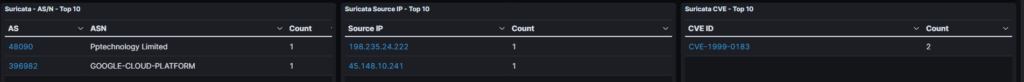
now that we have narrowed information of the attacker IP we can proceed to investigate.
In this lab I will pick the second IP to investigate, there are multiple sites we can use for our investigation such as Talos Blacklist, IPVoid Blacklist, in this example I will use Virus Total.
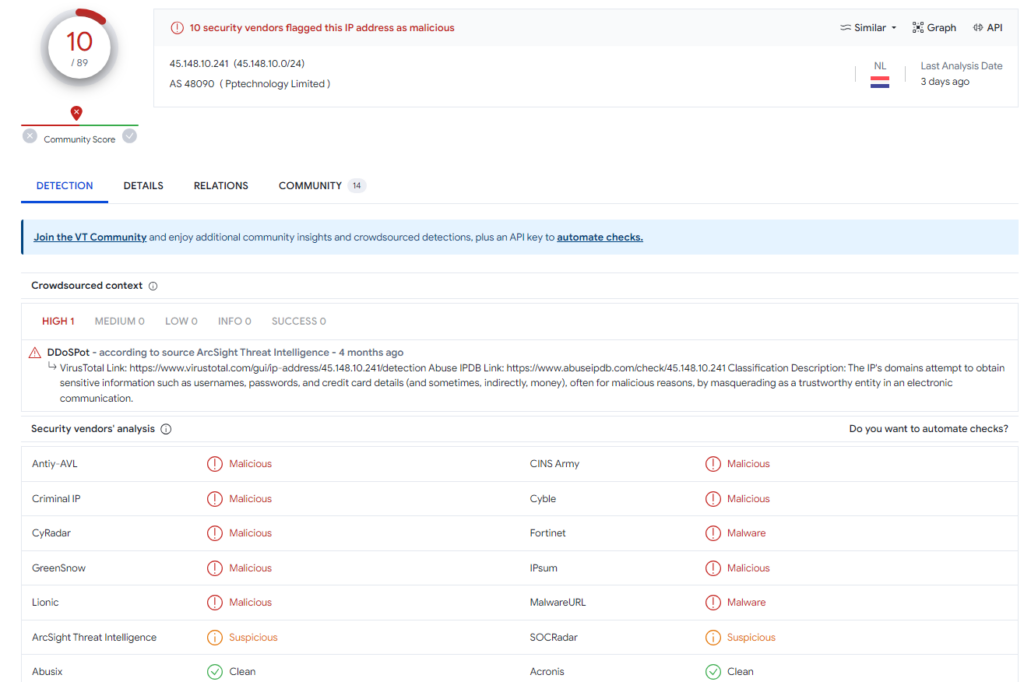
We can see IP address is blacklisted 10 security vendors and deemed suspicious in 2
going to the details tab and scrolling down to google results we can see that this IP address has a history as know bad actor involved in multiple attacks that range from DDOS, Port scanning, etc.
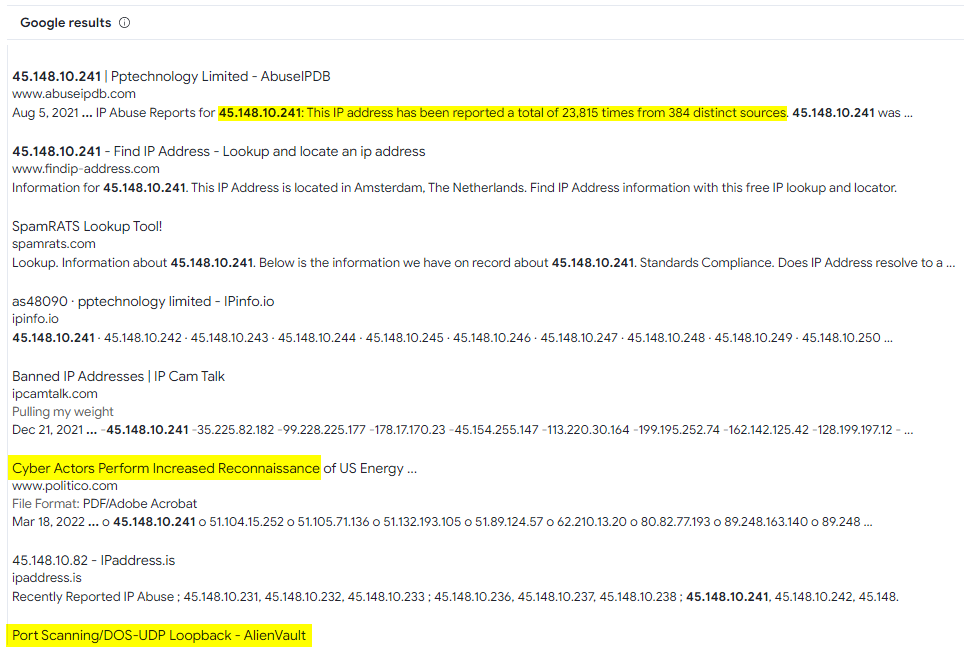
now lets investigate the CVE.
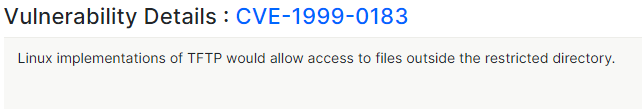
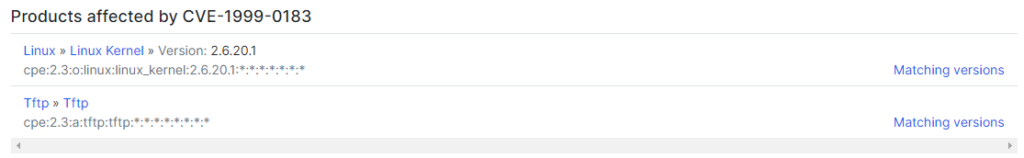
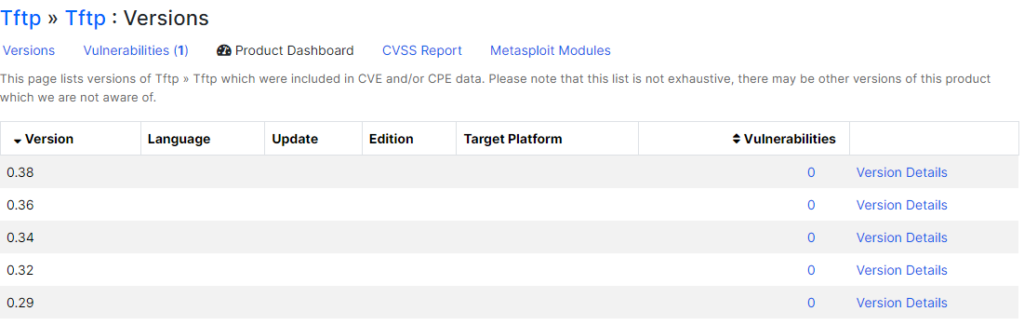
We can see that this attack affects Linux Kernel 2.6.20.1 and TFTP versions 0.38, 0.36, 0.34, 0.32, 0.29.
Recommended actions:
Block/Blacklist attacker IP address as a known bad actor.
Verify that there are no systems running on Linux Kernel 2.6.20.1 or using TFTP version 0.38, 0.36, 0.34, 0.32, 0.29.
Resolution:
No systems in my environment running vulnerable products or services.
Not deemed a threat, attack can be filtered from view.
