Create VM with the following specifications:
VM
Image: Debian 11 “Bullseye” – x64 Gen2
Size: Standard_D4S_V3 – 4 vcpus, 16 GiB memory
Data
Data disk (create and attach a new disk)
Size 128 GiB Premium SSD LRS
Network
leave default config
Management
leave default config
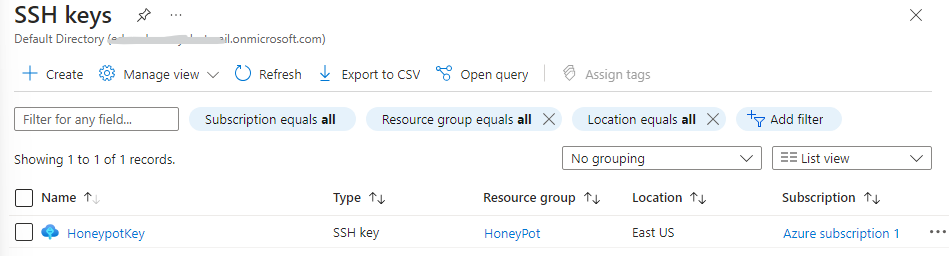
Make sure you create an SSH key for your resource group, you can do so by typing SSH Keys on azure search bar, create and download your SSH key.
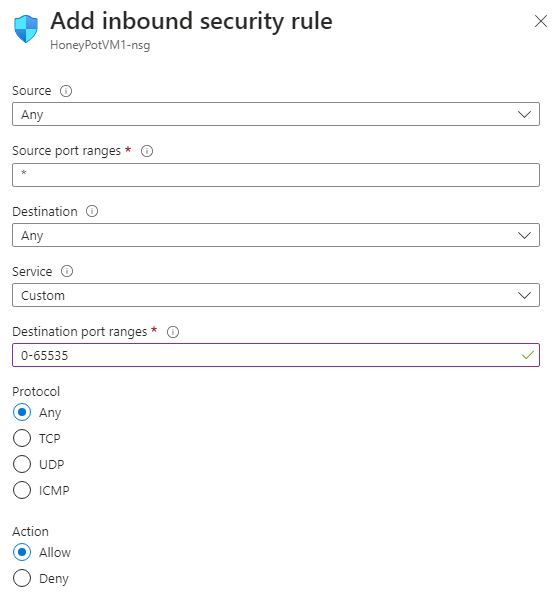
Go to your newly created honeypot vm and open the tab networking under settings
- since this is a honey pot and for this lab purpose, create an inbound security rule to open all ports
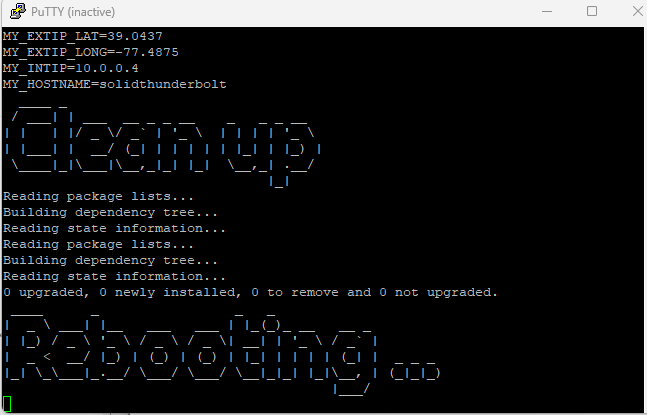
Now use putty to connect through SSH to your honeypot VM, use your VM’s NIC’ public IP to connect with putty.
- enter your credentials
- once logged enter the following commands to update your VMs OS:
-
sudo apt update sudo apt update-y
now we need to install git, use the following commad:
sudo apt install git
We will use and deploy the T-Pot platform for our lab which can be found on the following link, use command below install T-Pot on VM.
- https://github.com/telekom-security/tpotce
sudo git clone https://github.com/telekom-security/tpotcecd tpotce/iso/installer/sudo ./install.sh --type=user- select Y
- select standard installation
- create your user name and password to log in to T-Pot
T-pot honeypot is now successfully installed on the Azure VM.
now lets access our T-pot honeypot interface using our public IP, designated port:
https://xxx.xxx.xxx:64297
enter your credentials and you should be able to login to the t-pot honey pot web interface.
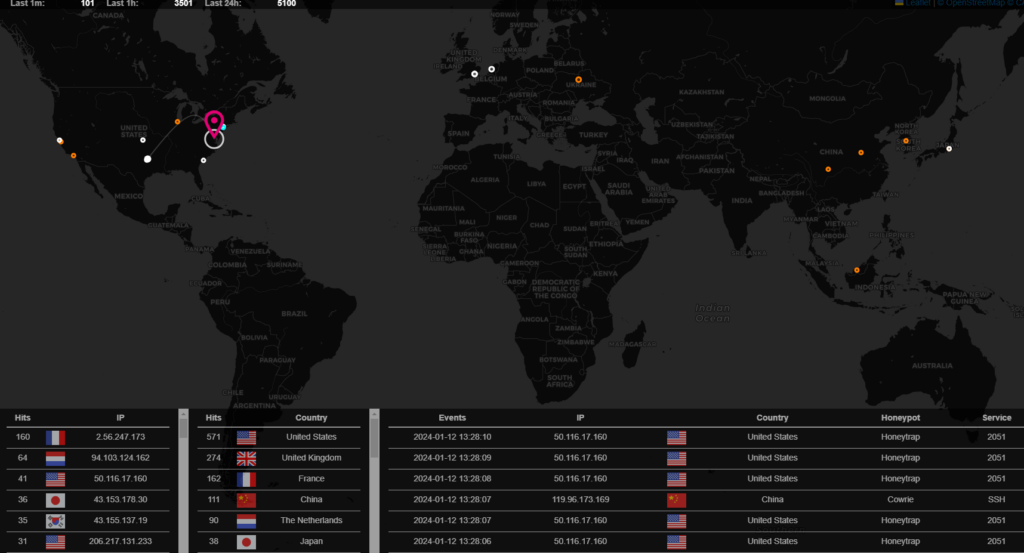
on attack map we can see Realtime attacks happening: